In addition to compromising individuals’ accounts, these cyberattacks can also pose significant consequences for businesses. Ponemon Institute recently reported that companies lose an average of $6 million each year to credential stuffing incidents through application downtime, lost customers, and heightened IT expenses. Further, these cyberattacks are on the rise. According to research from software company Arkose Labs, more than 2.8 billion credential stuffing incidents occurred in 2021, representing a 98% increase from 2020. As such, businesses need to take steps to protect against these cyberattacks.
How Credential Stuffing Incidents Work
A credential stuffing cyberattack generally takes place in four main phases. Here’s a breakdown of those phases:
- Obtaining login credentials—First, a cybercriminal will compile a list of stolen usernames and passwords from several victims. The cybercriminal may obtain these login credentials in various ways, such as deploying phishing scams or purchasing them on the dark web. According to a recent audit conducted by security firm Digital Shadows, more than 15 billion stolen usernames and passwords are circulating on the internet stemming from nearly 10,000 data breaches.
- Setting up a botnet—Next, the cybercriminal will input their list of stolen login credentials within a robot network, also called a botnet. A botnet is a collection of devices injected with malware to be controlled by a single party and leveraged in cyberattacks. The cybercriminal will use the botnet to test the stolen usernames and passwords against multiple websites and systems at once, searching for possible matches.
- Identifying successful login attempts—After using the botnet to test stolen usernames and passwords, the cybercriminal will note any successful login attempts and review the accounts or systems they have gained access to.
- Compromising accounts, systems, and data—Lastly, the cybercriminal will leverage their unsolicited access to victims’ accounts and systems to engage in various harmful activities. These activities may include changing account settings, taking over systems, exposing sensitive information, making fraudulent purchases, transferring funds, or conducting further cyberattacks.
Why Credential Stuffing Incidents Are on the Rise
In recent years, credential stuffing cyberattacks have become a growing concern, increasing cost and frequency. There are several reasons behind this trend, including the following:
- Greater credential availability—A surging number of login credentials have been exposed online over the past few years, mainly due to a rise in data breaches. As a result, cybercriminals have been granted more accessible access to stolen usernames and passwords, making credential stuffing incidents increasingly common.
- Further technology advancements—The technology utilized to conduct credential stuffing cyberattacks, such as botnets and similar automation tools, has also advanced over time. These technology developments have helped cybercriminals bypass traditional login security measures across different devices and systems and increase the speed at which they can test stolen credentials. Altogether, such advancements have allowed cybercriminals to boost the efficiency and simplicity of credential stuffing incidents.
- Reduced entry barriers—In response to the previously mentioned developments, the overall costs and skills required to conduct credential stuffing incidents have fallen, lowering entry barriers and permitting a larger pool of cybercriminals to launch these cyberattacks. Cybersecurity experts estimate that a credential stuffing incident can be deployed for as little as $50.
- Increased remote work issues—The proportion of remote workers has skyrocketed in the last couple of years—a trend that is expected to continue for the foreseeable future. Yet, many remote employees lack the same security capabilities within their home offices and personal devices compared to their workplace offerings, making them more vulnerable to cyberattacks (including credential stuffing incidents).
- Added detection difficulties—To help identify and combat cyberattacks, many individuals and businesses have installed various security software on their technology. However, because credential stuffing incidents involve cybercriminals using genuine usernames and passwords and impersonating legitimate parties, these cyberattacks have proven more challenging for specific software to detect and fight against. These detection difficulties have subsequently made credential stuffing incidents a more attractive attack method among cybercriminals.
Examples of Credential Stuffing Incidents
Multiple notable credential stuffing cyberattacks have occurred within the last few years, affecting several well-known businesses, their employees, and their customers. Some of these incidents include:
- Marriott International—In 2018, the hospitality company Marriott International experienced a credential stuffing cyber attack when a hacker obtained two employees’ login details and used them to compromise sensitive data belonging to more than 5 million customers stored within company systems.
- Zoom—During the rise of remote work and videoconferencing in 2020, cybercriminals launched a credential stuffing incident against software company Zoom, stealing 500,000 customer usernames and passwords and selling this information to online crime forums.
- Nintendo—In 2020, hackers deployed a credential stuffing cyberattack against video game company Nintendo, resulting in account takeovers and financial losses for 160,000 customers.
- Spotify—In 2021, audio streaming company Spotify faced a credential stuffing incident when cybercriminals obtained login details from a malicious database to compromise more than 100,000 customers’ accounts.
Considering these cyberattacks and their associated consequences, it’s evident that businesses need to implement measures to help prevent and mitigate potential losses stemming from credential stuffing incidents.
Steps Businesses Can Take
Businesses should consider the following measures to effectively avoid and minimize damages resulting from credential stuffing cyberattacks:
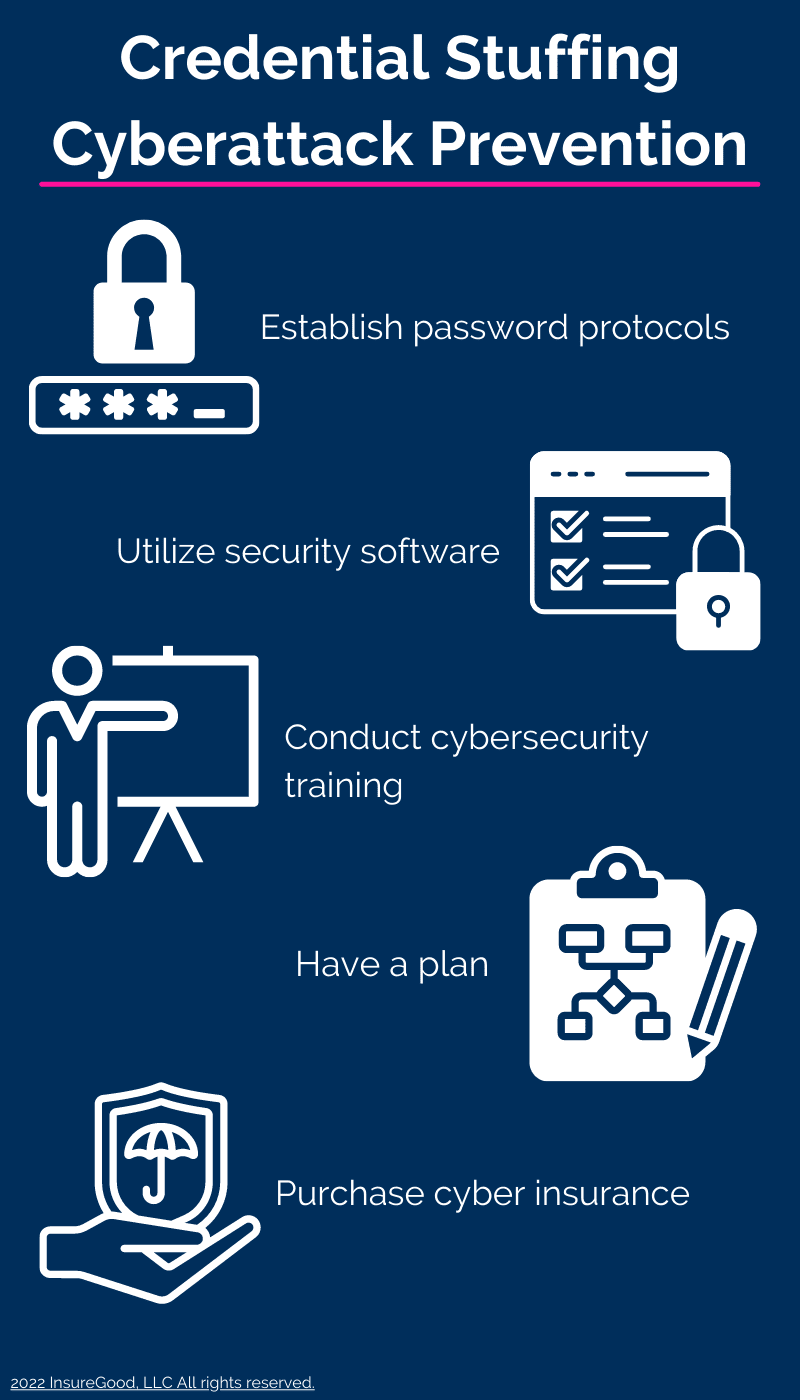
- Establish password protocols. Require employees to create complex and unique passwords for all workplace accounts and systems. These passwords should vary between each individual account and system to help reduce the likelihood of credential stuffing incidents. It may also be valuable to provide employees with access to password management programs to keep track of their credentials.
- Utilize effective security software. Certain security software can be particularly useful in identifying and mitigating credential stuffing cyberattacks. Such software includes botnet detection technology, website application firewalls, internet traffic filters and multifactor authentication tools. This software should be installed on all workplace devices and updated regularly to ensure effectiveness. Employees should also be required to utilize this software on personal devices if they use such technology for work purposes.
- Conduct cybersecurity awareness training. Employees should receive routine training on potential cyberthreats and ways to mitigate them. In the context of credential stuffing incidents, it’s crucial to educate employees on the importance of maintaining proper password hygiene, keeping up with security software updates and looking for signs that their accounts or systems may have been compromised (e.g., changed settings, modified data, unsolicited purchases or missing funds).
- Have a plan. Establishing a cyber incident response plan can help ensure necessary procedures are taken when cyberattacks occur, thus keeping related damages at a minimum. This plan should be well-documented, practiced regularly and address a range of cyberattack scenarios (including credential stuffing incidents).
- Secure sufficient coverage. Finally, it’s critical to purchase adequate cyber insurance to help protect against losses that may arise from credential stuffing incidents. It’s best to consult a trusted insurance professional to discuss specific coverage needs.
In addition to compromising individuals’ accounts, these cyberattacks can also pose significant consequences for businesses. Ponemon Institute recently reported that companies lose an average of $6 million each year to credential stuffing incidents through application downtime, lost customers, and heightened IT expenses. Further, these cyberattacks are on the rise. According to research from software company Arkose Labs, more than 2.8 billion credential stuffing incidents occurred in 2021, representing a 98% increase from 2020. As such, businesses need to take steps to protect against these cyberattacks.
How Credential Stuffing Incidents Work
A credential stuffing cyberattack generally takes place in four main phases. Here’s a breakdown of those phases:
- Obtaining login credentials—First, a cybercriminal will compile a list of stolen usernames and passwords from several victims. The cybercriminal may obtain these login credentials in various ways, such as deploying phishing scams or purchasing them on the dark web. According to a recent audit conducted by security firm Digital Shadows, more than 15 billion stolen usernames and passwords are circulating on the internet stemming from nearly 10,000 data breaches.
- Setting up a botnet—Next, the cybercriminal will input their list of stolen login credentials within a robot network, also called a botnet. A botnet is a collection of devices injected with malware to be controlled by a single party and leveraged in cyberattacks. The cybercriminal will use the botnet to test the stolen usernames and passwords against multiple websites and systems at once, searching for possible matches.
- Identifying successful login attempts—After using the botnet to test stolen usernames and passwords, the cybercriminal will note any successful login attempts and review the accounts or systems they have gained access to.
- Compromising accounts, systems, and data—Lastly, the cybercriminal will leverage their unsolicited access to victims’ accounts and systems to engage in various harmful activities. These activities may include changing account settings, taking over systems, exposing sensitive information, making fraudulent purchases, transferring funds, or conducting further cyberattacks.
Why Credential Stuffing Incidents Are on the Rise
In recent years, credential stuffing cyberattacks have become a growing concern, increasing cost and frequency. There are several reasons behind this trend, including the following:
- Greater credential availability—A surging number of login credentials have been exposed online over the past few years, mainly due to a rise in data breaches. As a result, cybercriminals have been granted more accessible access to stolen usernames and passwords, making credential stuffing incidents increasingly common.
- Further technology advancements—The technology utilized to conduct credential stuffing cyberattacks, such as botnets and similar automation tools, has also advanced over time. These technology developments have helped cybercriminals bypass traditional login security measures across different devices and systems and increase the speed at which they can test stolen credentials. Altogether, such advancements have allowed cybercriminals to boost the efficiency and simplicity of credential stuffing incidents.
- Reduced entry barriers—In response to the previously mentioned developments, the overall costs and skills required to conduct credential stuffing incidents have fallen, lowering entry barriers and permitting a larger pool of cybercriminals to launch these cyberattacks. Cybersecurity experts estimate that a credential stuffing incident can be deployed for as little as $50.
- Increased remote work issues—The proportion of remote workers has skyrocketed in the last couple of years—a trend that is expected to continue for the foreseeable future. Yet, many remote employees lack the same security capabilities within their home offices and personal devices compared to their workplace offerings, making them more vulnerable to cyberattacks (including credential stuffing incidents).
- Added detection difficulties—To help identify and combat cyberattacks, many individuals and businesses have installed various security software on their technology. However, because credential stuffing incidents involve cybercriminals using genuine usernames and passwords and impersonating legitimate parties, these cyberattacks have proven more challenging for specific software to detect and fight against. These detection difficulties have subsequently made credential stuffing incidents a more attractive attack method among cybercriminals.
Examples of Credential Stuffing Incidents
Multiple notable credential stuffing cyberattacks have occurred within the last few years, affecting several well-known businesses, their employees, and their customers. Some of these incidents include:
- Marriott International—In 2018, the hospitality company Marriott International experienced a credential stuffing cyber attack when a hacker obtained two employees’ login details and used them to compromise sensitive data belonging to more than 5 million customers stored within company systems.
- Zoom—During the rise of remote work and videoconferencing in 2020, cybercriminals launched a credential stuffing incident against software company Zoom, stealing 500,000 customer usernames and passwords and selling this information to online crime forums.
- Nintendo—In 2020, hackers deployed a credential stuffing cyberattack against video game company Nintendo, resulting in account takeovers and financial losses for 160,000 customers.
- Spotify—In 2021, audio streaming company Spotify faced a credential stuffing incident when cybercriminals obtained login details from a malicious database to compromise more than 100,000 customers’ accounts.
Considering these cyberattacks and their associated consequences, it’s evident that businesses need to implement measures to help prevent and mitigate potential losses stemming from credential stuffing incidents.

Steps Businesses Can Take
Businesses should consider the following measures to effectively avoid and minimize damages resulting from credential stuffing cyberattacks:
- Establish password protocols. Require employees to create complex and unique passwords for all workplace accounts and systems. These passwords should vary between each individual account and system to help reduce the likelihood of credential stuffing incidents. It may also be valuable to provide employees with access to password management programs to keep track of their credentials.
- Utilize effective security software. Certain security software can be particularly useful in identifying and mitigating credential stuffing cyberattacks. Such software includes botnet detection technology, website application firewalls, internet traffic filters and multifactor authentication tools. This software should be installed on all workplace devices and updated regularly to ensure effectiveness. Employees should also be required to utilize this software on personal devices if they use such technology for work purposes.
- Conduct cybersecurity awareness training. Employees should receive routine training on potential cyberthreats and ways to mitigate them. In the context of credential stuffing incidents, it’s crucial to educate employees on the importance of maintaining proper password hygiene, keeping up with security software updates and looking for signs that their accounts or systems may have been compromised (e.g., changed settings, modified data, unsolicited purchases or missing funds).
- Have a plan. Establishing a cyber incident response plan can help ensure necessary procedures are taken when cyberattacks occur, thus keeping related damages at a minimum. This plan should be well-documented, practiced regularly and address a range of cyberattack scenarios (including credential stuffing incidents).
- Secure sufficient coverage. Finally, it’s critical to purchase adequate cyber insurance to help protect against losses that may arise from credential stuffing incidents. It’s best to consult a trusted insurance professional to discuss specific coverage needs.
The Last Word
Ultimately, credential stuffing cyberattacks are a rising threat for all businesses, with the potential to progressively worsen going forward. Through the implementation of proper prevention and response measures, businesses can stay sufficiently protected from these incidents. For more risk management guidance, contact an InsureGood Advisor today.





